A JSON Web Token (JWT) is a small, URL-safe token type that offers web applications a safe method of managing user authentication. It consists of three components: the payload, signature, and header. Metadata like the signature technique and token type (JWT) are included in the header. User-specific information, or “claims,” such as user ID, are carried in the payload, and the signature confirms that the token hasn’t been altered, ensuring its authenticity and integrity. JWTs are particularly helpful in Node.js applications since they are lightweight and integrate effectively, which makes them perfect for protecting mobile apps, SPAs, and other platforms that need smooth authentication.
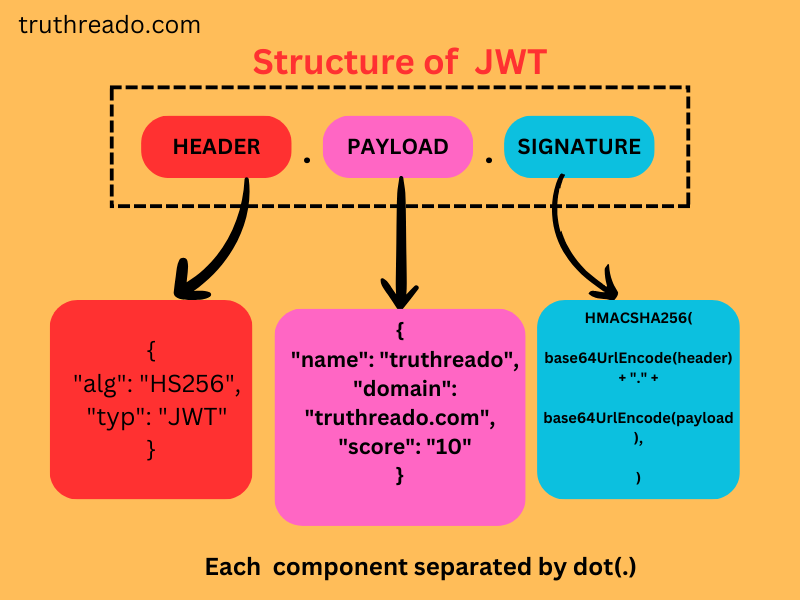
Structure of JWT
Encoded and Decoded:
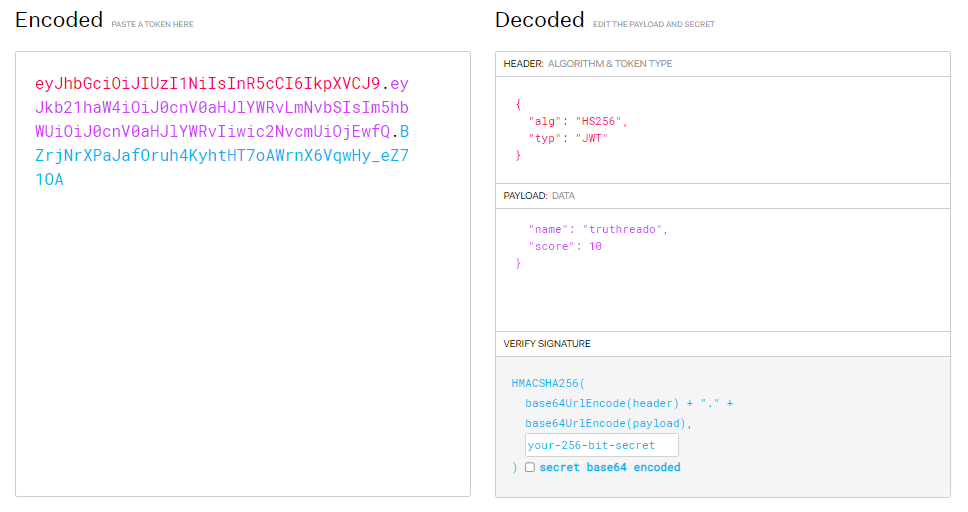
JSON Web Token (JWT) is a compact, URL-safe method for securely transmitting information between parties as a JSON object. It consists of three parts: the header, payload, and signature. Each part is base64 encoded to ensure safe transmission over HTTP.
Encoded JWT
After encoding, the JWT looks like this:
header.payload.signature
- Header: This holds information about the signing algorithm (alg) and the type of the token (typ). Example: { “alg”: “HS256”, “typ”: “JWT” }. It is Base64Url encoded.
- Payload: It contains the user’s claims or data (for example, user ID, and roles). Some of such claims can be registered, public, or private. Example: { “sub”: “12345”, “name”: “John” }. It is also Base64Url encoded, but it is not encrypted.
- Signature: It provides assurance of the integrity of the token. It is generated by signing the encoded header and the encoded payload using a secret key with the specified algorithm in the header, for example: HMAC SHA256. The signature prevents the token from being altered.
Decoded JWT
To decode a JWT, you can reverse the process:
- Base64 decode the header and payload.
- The signature cannot be decoded directly as it is just a hash of the header and payload.
- The decoded header and payload are returned in their original JSON form.
While decoding is easy, validation of the signature is crucial to ensure that the token hasn’t been tampered with. Libraries like jsonwebtoken in Node.js or pyjwt in Python provide built-in methods for encoding, decoding, and verifying JWTs.
In summary, JWT encoding provides a secure way to transmit data, and decoding allows extracting and using that data while maintaining integrity through the signature validation.
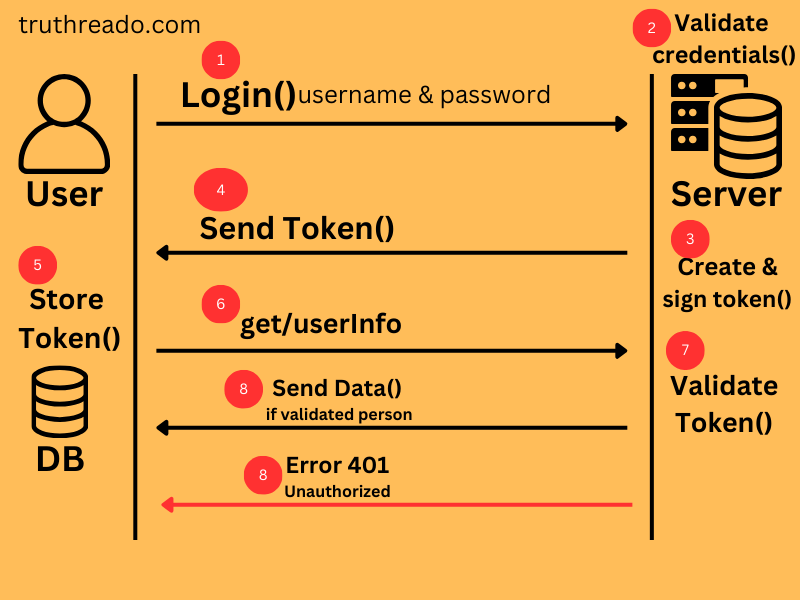
A typical JWT authorization flow consists of the following steps:
- Token Generation and Client Transmission: The JWT is created by the server and forwarded to the client, therefore preserving it for next use.
- Sending the Token to the Server: Token Delivery to the Server: The client adds the JWT to the HTTP request’s permission header to access a guarded resource on the server.
Axios.get(URL, { headers: { ‘Authorization’: ‘Bearer’ + token, }, }) - Authentication: The user logs in using their login and password, or with Google or Facebook, for example.
The credentials are verified by the server. - Verifying the Token: The server checks the validity of the request by use of the secret key applied to JWT signature. Should the data be accurate, the server gets it from the JWT to ascertain the kind of activities the user is free to engage in.
- Authorizing the Request: The server provides the requested information if the user is permitted access to the resource. The server produces an error message if the user is not permitted.
Advantages
- Lightweight
- Portable: can be processed on multiple platforms, web and mobile.
- JSON parsers are common in most programming languages.
- Protected against tampering because of the secret key stored on server side.
- The server does not need to store any session information, because of the stateless nature of the JWT token.
Disadvantages
- Should not store sensitive info.
- On client side should be store somewhere secure.
JWT official website
Conclusion
JWT offers a simple yet effective way to implement secure, stateless authentication in Node.js applications. With helpful npm packages like jsonwebtoken and bcryptjs, setting up authentication becomes straightforward, laying a strong foundation for secure user management. From this starting point, you can further enhance security and functionality by adding features like refresh tokens, database integration, and token expiration handling. These steps contribute to a reliable, scalable authentication solution that meets the demands of modern applications.
